New phishing attack uses real-time interception to bypass 2FA
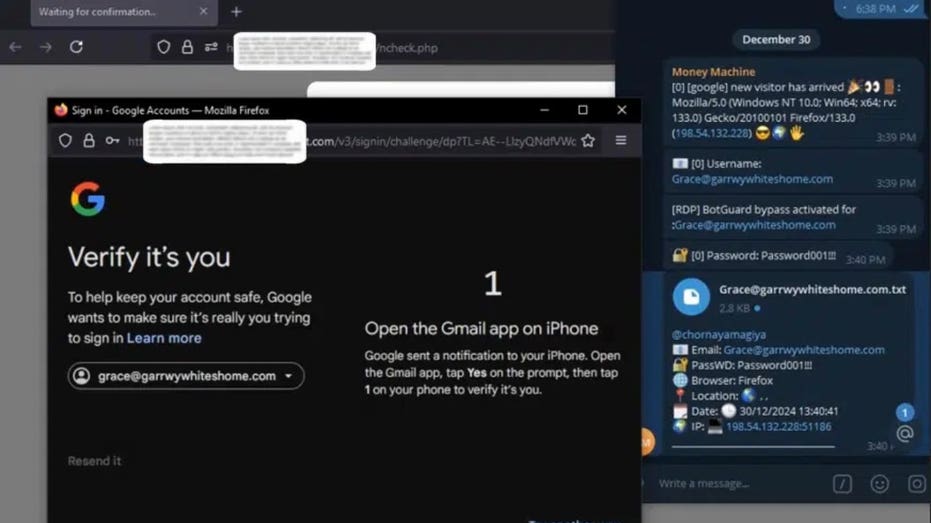
This phishing kit bypasses 2FA via session hijacking and real-time credential theft. Kurt “CyberGuy” Knutsson offers four ways to stay safe from Astaroth phishing attacks.

This phishing kit bypasses 2FA via session hijacking and real-time credential theft. Kurt “CyberGuy” Knutsson offers four ways to stay safe from Astaroth phishing attacks.